
A Practical Guide to Permissioned vs. Permissionless Blockchains
Written by Max Crawford
Most people picture blockchains as open networks where anyone can see the data, transact, or even launch their own project without anyone’s "permission."
And that’s true for networks like Bitcoin, Ethereum, and Solana. You could verify any Ethereum transaction right now or deploy a new token on Solana in the next 10 minutes.
But these very traits that make blockchains powerful (openness, transparency, and inclusivity) raise concerns for enterprises. Businesses operate in regulated environments where accountability, privacy, and control are essential. What they need from a blockchain is not complete openness, but structured governance and restricted participation.
To address these differing needs, blockchains have evolved into two main types: permissioned and permissionless blockchains.
In this article, you’ll learn what permissioned and permissionless blockchains are, how they differ, and what is the purpose of each.
What Are Permissionless Blockchains?
Permissionless blockchains (a.k.a. public or trustless blockchains) are open networks that anyone can join and participate in without prior approval.
In a permissionless blockchain, any node on the internet (say, your laptop) can become part of the network,, submit transactions, and take part in the consensus process that validates new blocks. This open-access design embodies the original decentralized vision of blockchain.
Also read: Pros and Cons of Running Your Own Node
The vast majority of blockchains you come across are permissionless blockchains. Think Ethereum, Solana, Cardano, Polkadot, etc.
Permissionless blockchain networks are ideal if you want to build a product or deploy a project that is open, community-driven, and accessible to anyone without restrictions.
Traits of Permissionless Blockchains
Open participation: Anyone can join the network without approval. You can run a node or build applications freely.
Decentralized governance: Decision-making is distributed among participants through consensus mechanisms and community proposals.
Transparency & auditability: All transactions and smart contract interactions are recorded on a public ledger that anyone can verify in real time.
Pseudonymity: Users are identified by wallet addresses, not real-world identities. This provides privacy without full anonymity (though some networks provide anonymity, too).
Censorship resistance: No authority can block, alter, or reverse legitimate transactions once they’re confirmed.
Native incentives: Participants are rewarded for securing and maintaining the network, aligning incentives for honest behavior.
Global accessibility: Anyone with an internet connection can participate regardless of geography, wealth, or status.
Security through consensus: Security comes from cryptography and distributed consensus (like Proof of Work or Proof of Stake), making it nearly impossible to manipulate the ledger.
What Are Permissioned Blockchains?
Permissioned blockchains are closed networks where access and participation are restricted to a predefined group of vetted participants. They are sometimes called private blockchains (if run by a single organization) or consortium blockchains (if governed by a group of organizations).
In permissionless chains, enterprises can set up hierarchical permissions. Meaning, participants can have distinct roles and access levels within the network for more control over security, governance, and data visibility.
For example, common applications of permissioned chains include requiring all users to submit identifying information for the purposes of KYC/AML or to limit who can see onchain data to internal staff only.
Permissioned blockchain networks are ideal if you want to build a product that is secure, controlled, and designed for trusted participants within a regulated environment.
Hyperledger Fabric (an open-source framework by IBM/Linux Foundation) and R3 Corda are popular platforms for permissioned blockchains.
Traits of Permissioned Blockchains
Restricted participation: Only approved entities can join the network or access specific data.
Centralized or consortium governance: Decision-making and rule-setting are handled by a central authority or consortium of members.
Known and verified identities: All participants have verified identities, often tied to real-world organizations or individuals.
Controlled privacy & confidentiality: Not all data is visible to everyone. Organizations can maintain commercial confidentiality of transactions.
Customizable consensus mechanisms: Since participants are trusted, these networks use lightweight consensus algorithms (like RAFT, PBFT, or IBFT).
Permission hierarchies: Different participants can have different roles for flexible governance and layered security.
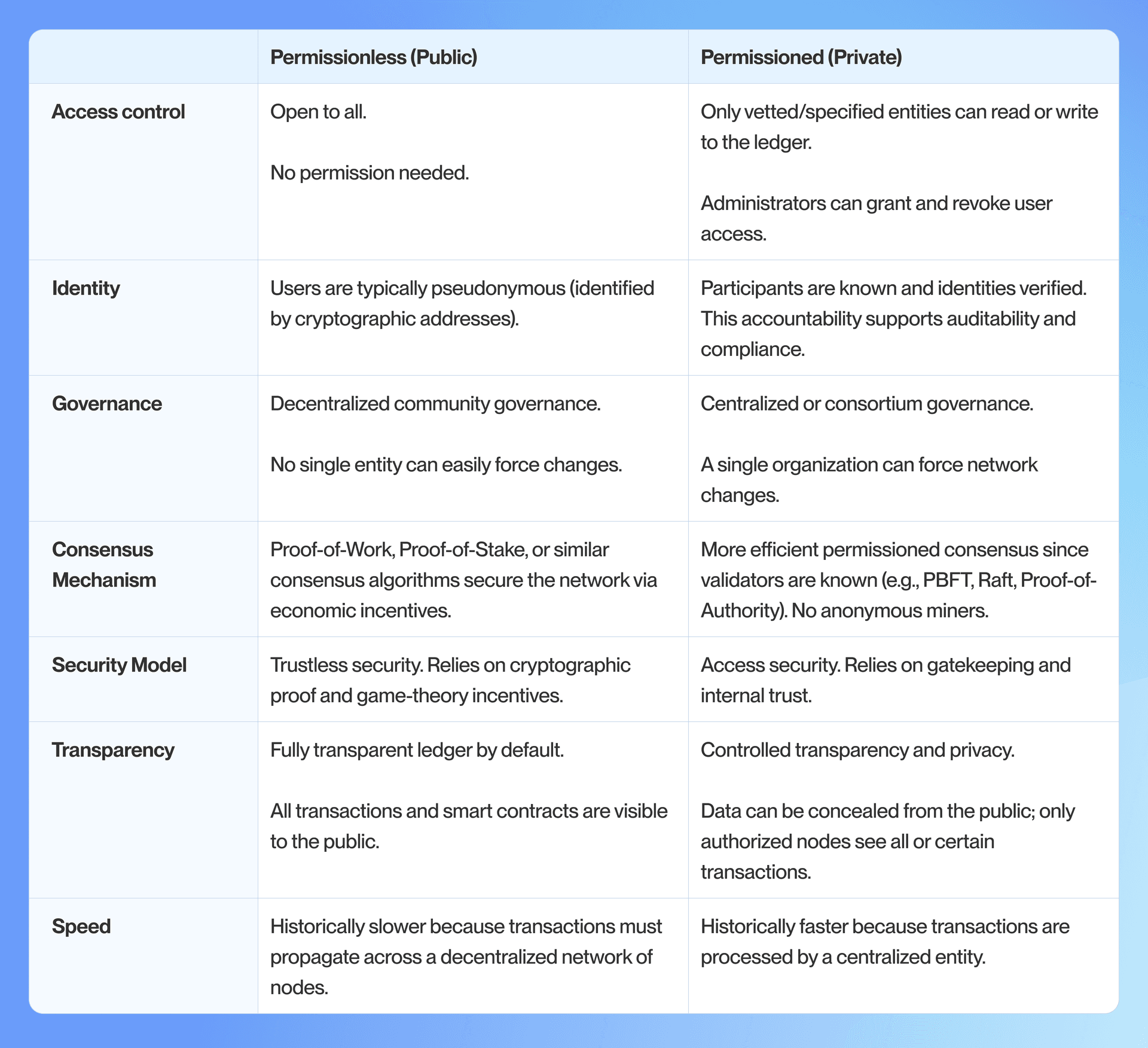
Key Differences of Permissioned vs. Permissionless Blockchains
Both permissionless and permissioned blockchains use distributed ledger technology. But, they differ in how they balance openness, trust, and control. The following table summarizes the key differences across critical dimensions:
Benefits of Permissionless Blockchains
1. Global Access
Anyone with an internet connection can join a permissionless network. That freedom invites users and capital from everywhere, accelerating innovation and network effects.
2. Open Source Flywheel
A byproduct of open access is developer network effects: these networks are open source and encourage other developers to build with or on your product. Depending on what you’re building, that flywheel could make or break your project.
3. Stable Foundation
No single company or government can easily force protocol changes. By resisting unilateral control, permissionless blockchains get long term international credibility and better network resiliency.
4. Security by Network
Permissionless blockchains rely on game theory and have mechanisms in place that are designed to ensure everyone plays fair. At a high level, this means that a sufficiently decentralized network is actually more secure than its centralized counterpart, and everyone is incentivized to maintain an honest network.
Disadvantages of Permissionless Blockchains
1. Unpredictable Fees
With open accessibility comes a lack of predictability. In public chains, block space is shared among all users and apps. Every transaction competes for inclusion in the next block. So, your users’ experience is never fully in your hands. A surge in activity can lead to very high transaction fees or delayed confirmation times
2. Risk of Attacks and Protocol Exploits
Openness cuts two ways: anyone can use the network, for good or bad. If you’re building a product on a permissionless blockchain, you have to invest in audits and fail-safes. Every line of code is a potential attack surface for a bad actor.
3. Lack of Privacy
Transparency is great for auditability, but it’s a big bug if privacy is important to your users or use case. Every transaction and address is visible on-chain.
Enterprises handling sensitive data (e.g., financial assets or identity management) may not be able to operate directly on public blockchains. And if they do, then they need to adopt complex technologies like zk-SNARKs or off-chain encryption.
Benefits of Permissioned Blockchains
1. Controlled Participation and Compliance
Permissioned blockchains allow only verified and approved participants to join. This makes them naturally aligned with regulatory and compliance requirements such as KYC, AML, and GDPR, which are critical for some enterprise and government applications.
This control over participation makes permissioned blockchains suitable for enterprises in heavily regulated industries.
2. Enhanced Privacy and Confidentiality
Network access is customizable, and you can specify who can see what data. This is a crucial feature for companies operating in highly regulated industries that need to protect user data, or trade secrets.
3. Greater Accountability
Because participants are known entities, misbehavior can be traced to real people (or entities) with surprising ease. This creates a strong deterrent against malicious activity, and when you find it, you can actually remove the responsible party from the network.
4. Stable network fees
Since permissioned chains often work as “appchains” serving a single use case, you don’t have to worry about other network participants or apps causing congestion or spikes in fees, that in turn impact your users. Instead, permissioned networks generally enjoy lower transaction fees, higher throughput, and better UX.
Disadvantages of Permissioned Blockchains
1. Centralization Risk
In permissioned networks, governance is handled by a set of administrators, introducing single points of failure. If that central entity is compromised, so is the entire network.
2. Reduced Transparency and Auditability
In permissioned environments, private ledgers are not accessible to external observers. So, while privacy is enhanced, public verifiability is lost. This might reduce public trust in your chain, and slow market adoption.
3. Higher Cost and Maintenance Burden
Without a public incentive layer (like block rewards), the maintainers of a permissioned network must fund its infrastructure, security, and governance directly. Consequently, that comes with higher overhead and costs, more so than building on an open network. And when maintaining a network at scale, enterprise may find that they need a lot of expertise in order to deliver the performance and reliability their users expect.
Get The Best of Both with Alchemy Rollups
Permissioned and permissionless blockchains each have unique strengths and weaknesses. And some teams want such a mix of features that neither blockchain offers independently.
For example, an enterprise may want the openness of a public network but with the control of a private network. With Alchemy Rollups, they can have both.
A rollup is essentially a separate blockchain that batches transactions and settles them onto a main network like Ethereum. That means you can set up custom rules, access controls, and performance parameters while still inheriting Ethereum’s security, transparency, and auditability.
Also read: What Are Rollups-as-a-Service and Appchains?
Real-World Examples of Enterprises Using Permissionless Blockchains
1. Coinbase pioneers with Base
One emerging trend is not only enterprises building on permissionless blockchains, but launching their own chain altogether. With over $4.5B in TVL, Coinbase’s Base chain is perhaps the most successful example of this to date, providing a network for Coinbase to onboard users, integrate their products onchain, and generate revenue.
2. Stripe Announces Tempo
In September this year, Stripe and Paradigm announced a new payments-focused L1 called Tempo. With $500M in funding and the support of one of the largest merchant processors in the world, this project is a clear signal that enterprise payment rails are moving onchain.
3. Figure Technology Solutions: Lending & RWAs
Figure Technology Solutions operates lending and asset-tokenization infrastructure on Provenance Blockchain (a public protocol designed for financial services). It has broad institutional partners, tokenized real-world assets, and uses a public-chain architecture rather than a purely private ledger.
Real-World Examples of Enterprises Using Permissioned Blockchains
1. SWIFT: Blockchain-Based Cross-Border Payments
SWIFT is adding a blockchain to its core infrastructure to improve settlement speed and transparency of international payments. Built in collaboration with over 30 major financial institutions, the ledger operates as a permissioned network that enables real-time, 24/7 cross-border transactions for tokenized regulated assets.
2. London Stock Exchange Group: Blockchain-Powered Fundraising
The LSEG became the first major stock exchange in the world to launch a system that’s fully powered by blockchain. It completed its first blockchain-powered fundraising through an open-access infrastructure that supports issuance, trading, and settlement on a single network.
3. Hitachi: Procurement Smart Contracts
Hitachi had a procurement process involving approximately 3,500 supplier companies, with manual contract handling, paperwork, and fraud/inefficiency risks. So, the company implemented a permissioned blockchain solution using Hyperledger Fabric to support paperless procurement contracts and transactions. The result was improved security and reduced the dependency on paper processes while handling at least one contract per company per month in a streamlined way.
Conclusion
Whether you are going to be building on public or private chains, it’s important to familiarize yourself with the enterprise blockchain tech stack. Both permissionless and permissioned blockchains have proven their worth in recent years, but in different arenas.
Choose permissionless if you want anyone, anywhere to use or build on your product. In this open-source setting, your app becomes part of a global ecosystem where developers, partners, and users can extend what you’ve started.
Choose permissioned if you need to control network access and data permissions. This is for banks, fintechs, or enterprises that have to follow KYC and privacy rules, or just want to use blockchain to make internal operations more efficient.
Frequently Asked Questions
What is the difference between permissionless blockchain and permissioned blockchain?
The main difference lies in access control. A permissionless blockchain is open to anyone. A permissioned blockchain, on the other hand, restricts participation to verified entities approved by an administrator.
Why would an enterprise need a permissioned chain?
Enterprises need permissioned blockchains to share data securely and stay compliant. They get blockchain’s transparency and efficiency while controlling who can access, validate, or view sensitive information, crucial for regulated sectors like finance.
Is Ethereum permissioned or permissionless?
Ethereum is a permissionless blockchain. Anyone can create a wallet, deploy smart contracts, or run a node without needing approval.
What is an example of a permissioned blockchain?
A modern example of a permissioned blockchain is SWIFT’s new shared ledger, built for global banks to settle payments securely while keeping full control and compliance. Other examples include LSEG’s Digital Markets Infrastructure, which uses private ledgers for regulated asset transfers and settlements.
What does "permissionless" mean in blockchain?
“Permissionless” means that no authorization is required to access or interact with the blockchain. Anyone can join and participate in the network.

Related overviews
Looking for the best Hyperliquid RPC in 2026? This guide showcases the best providers.
Learn about the role of indexers and how they help you query onchain data.
Looking for service providers that make building onchain easy? Meet the top players here.

Build blockchain magic
Alchemy combines the most powerful web3 developer products and tools with resources, community and legendary support.